MITRE ATT&CK
Standardized framework for translating security data and practises into business effect. Use advanced threat intelligence to outmanoeuvre opponents
What factors make MITRE ATT&CK more relevant than ever?
As waves of cybersecurity breaches continue to strike enterprises, this globally-recognized and -accessible but grossly underused information repository is gathering pace. MITRE Corporation, a non-profit organisation, established the framework based on real-world observations to record and monitor the varied methods and approaches used by attackers at various phases of entering a network and exfiltrating data.
As the most broad, comprehensive, accurate, and full knowledge base, this framework offers public, commercial, and non-profit organisations a systematic, data-driven way to assess security controls and identify security management gaps for the purpose of rectification.
Make It the foundation of your security process
If you are wondering why your security controls are unable to stop attacks or why similar attacks are successfully evading your security measures despite having a workflow in place, the answer may lie in the absence of a system that effectively interprets the organization’s threat intelligence and takes the appropriate actions.
Nonetheless, when you construct your security workflow using the ATTACK architecture as its central component, you establish a solid framework that comprehends and extracts vital insights from the organization's threat information. The methodology synthesises all data and threat intelligence to answer the three most essential questions: attacker location, attacker motivation, and attacker goal.
In addition, the framework prohibits attackers from misusing system services to remotely execute commands, manipulate distant services, or execute malicious applications remotely. Windows service control manager is one of the system services often exploited to execute malicious instructions because it allows the management or modification of Windows services and newly generated services. In addition to the service control manager API, additional service execution tools like PsExec are often used for service execution.
Using the framework's proposed mitigation approaches, businesses may also identify and prevent events that signal a software exploit. Features such as Attack Surface Reduction (ASR) and Microsoft Enhanced Mitigation Experience Toolkit (EMET) may be used to avoid similar tactics and circumvent application control. Permit defence surface decrease
Key Obstacles in Utilizing MITRE ATTACK
While the framework is of tremendous assistance in comprehending opponents and their strategic methods of infiltrating a system, applying it may be incredibly difficult for businesses because to its size, complexity, and extensive data variations. Lack of automation in processing this huge volume of data and mapping it against an organization’s security architecture is an additional demanding undertaking that stops enterprises from implementing this universal framework to its full potential.
Not every method is necessarily harmful. How to achieve parity, reduce warnings, and prioritise threats
Not every approach is easily detectable. How to deploy state-of-the-art methods to identify and look for hidden threats
Several strategies have a variety of potential implementations. How to use sub-techniques to overcome this issue.
Some approaches are classified under numerous strategies because they are applicable to many use cases and assault phases.
Value Maximization using CDWT
At CDWT, the world’s largest provider of application-focused managed cloud services and a leading cybersecurity partner, we employ the ATTACK framework to make every security solution intelligent and objective-oriented in order to outmaneuver attackers and maximize threat intelligence. Here is a strategic example of how we utilize the architecture to provide improved threat identification and enhanced protection against threat actors that are continually evolving:
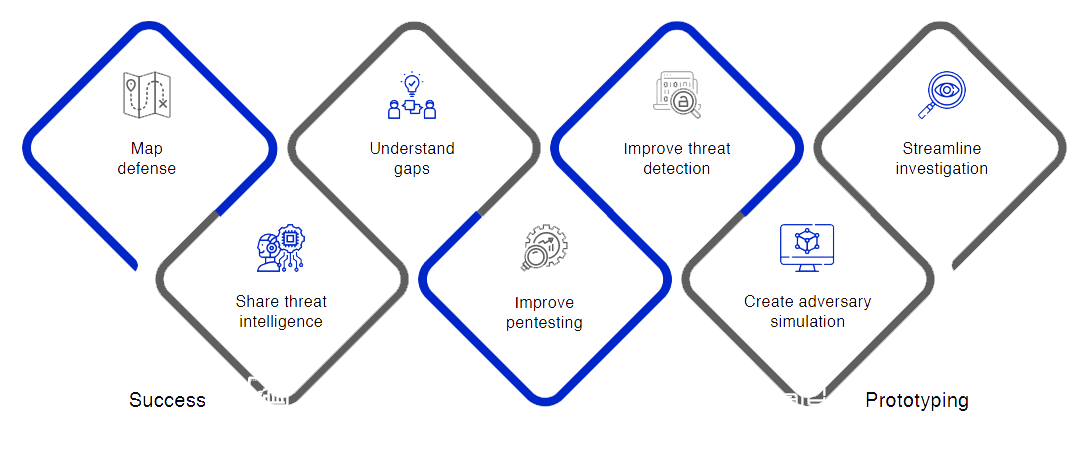
Decode Attacker Tactics: Comprehend an Attacker’s Strategic Objective
The first crucial stage in constructing a defense against adversaries is to comprehend the danger actor’s purpose or strategic objective. It might include demanding a ransom, stealing extremely sensitive data, or ruining an IT infrastructure. An attacker develops a series of short-term objectives to accomplish the objective, beginning with getting early access to lateral movement or command and control. Listed below is a categorization of different attack techniques outlined by the framework to aid comprehension of the attacker’s intent:
|
Tactic
|
Aim
|
|---|---|
|
Reconnaissance
|
Collect essential data for future operations
|
|
Resource development
|
Develop assets to support future activities
|
|
Initial access
|
Invade/penetrate the network
|
|
Execution
|
Run harmful code
|
|
Persistence
|
Maintain their standing
|
|
Privilege escalation
|
Obtain higher-level authorizations
|
|
Defense evasion
|
Remain unnoticed
|
|
Credential access
|
Theft of credentials
|
|
Discovery
|
Determine the environment
|
|
Lateral movement
|
Navigate the surroundings.
|
Recognizing the Leading Use Cases
This worldwide threat information database may be used in a variety of ways. Here are the six most important use cases for the framework’s intelligence:
Threat emulation
Red teaming or pentesting
Behavioral analytics development
Defensive gap assessment
SOC maturity assessment
Cyber threat intelligence enrichment
Advanced Management, Detection, and Response Capabilities
CDWT uses the ATTACK framework to speed up threat management, detection, and response (MDR) across networks, endpoints, applications, and infrastructure. MDR is a fundamental component of CDWT’s Managed Security Services. By integrating threat intelligence with powerful automation capabilities, CDWT enables businesses to enhance SOC efficiency, mitigate cyber assaults, and react to threats more quickly.
Enabling Top Security Frameworks
Threat Hunting and Detection at Depth
Automated Protection Measures
Analytics for Threat Behavior
Superior Threat Intelligence
Identity and Access Administration
Endpoint Security Administration
Cloud Security Administration





