SecOps Services and Solutions
Adopt security-by-design. Integrate security and operations teams into the organization’s operations and development processes for on-premises and various cloud environments.
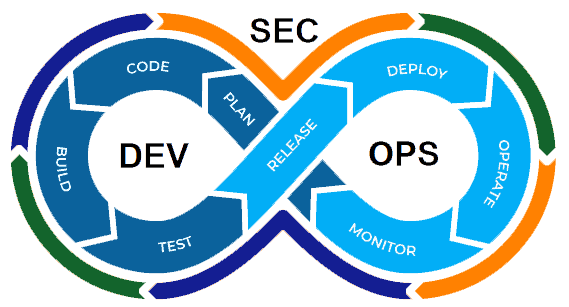
SecOps (Security and IT Operations): The union for continuous availability and enhanced resilience
An organization’s mismatched practises account for 99 percent of security risks. 79% of organizations that have had a single security breach have disclosed that a standard patch or setting in their development procedures may have averted the occurrence.
The aforementioned statistics speak loudly about the disjointed daily activities of development, operations, and security teams, which severely impede agility, speed to market, and advancement. The majority of the time, operational teams strive to get software to market and meet business goals, while development teams envisage producing the ideal piece of code to hand over to their ownerships.
A third complexity comes when security operations teams and engineers using distinct solutions, platforms, and procedures scan the whole code and halt critical modules operating core systems owing to newly discovered vulnerabilities. The answer is straightforward: merge development, operations, and security teams into a single, collaborative process known as DevSecOps.
DevSecOps combines DevOps and SecOps, two groups, individuals, processes, and techniques that are quite prominent in the IT business today. While the first mandates the alignment of a company’s software, app, and solution development teams with its Operations team, the second mandates strong coordination between IT security and IT operations.
Why SecOps and what is Cloud SecOps (SecOps on Cloud)?
SecOps (Security Operations) implements security by design, which enables Operations teams and developers to be aware of vulnerability management across the whole process. This enables periodic asset monitoring, assessments, compliance audits, threat detection, and remediation planning across all business IT systems, platforms, applications, software, virtual machines (VMs), and cloud environments. While continuous process output and security checks may seem to impede time-to-market and productivity, they really protect businesses against several iterations, compliance-related issues, and huge breaches. The positives far outweigh the drawbacks.
DevSecOps and SecOps solutions and services are at the core of CDWT's security management capabilities, as the world's biggest application-focused managed cloud services provider and a leading cybersecurity firm. CDWT not only helps align people, processes, and resources to quickly adopt a SecOps and DevSecOps approach, but also provides hyper-agile, highly scalable, and profoundly secure performance across all IT operations and workflows. It's the finest of all possible universes.
Benefits of Implementing a SecOps (Security Operations) Methodology or Team:
Consolidate security goals and priorities throughout all development and operational activities in accordance with industry standards.
Integrated communication and risk management methods at every organizational process phase
Management of security that is proactive, encompassing discovery, analysis, and response to threats in an agile manner across all corporate systems and cloud environments.
Integration of SecOps automation tools and security operations solutions throughout product development, app creation, operational processes, cloud workloads, and other phases.
Regular vulnerability evaluations at each phase of development, delivery, and operating procedures.
To transition into a more agile delivery and operations model, optimization is used to eliminate redundancies, time-consuming processes, and dangerous procedures.
Regular compliance checks and audits to verify that all processes adhere to national and international norms and laws, in accordance with best practises in the industry.
Effective change management to implement updated security checks and tools for all system, process, and environment modifications.
Advantages of Cloud SecOps
Powered by cloud storage, SecOps or DevSecOps activities that are highly scalable and flexible throughout the whole environment.
Deployment of effective cloud-native tools and technologies for security automation and incident management across the development, security, and operations environments.
Establish productive coordination and uniformity across all web, app, and software development, operations, and security teams.
To improve workflows and delivery, eliminate duplicate protocols, techniques, and procedures amongst the development, security, and operations teams.
Integrate structured, sophisticated SecOps solutions, platforms, tools, and procedures to accelerate the organization-wide deployment of a SecOps and DevSecOps culture.
Incorporate innovative security automation, such as CI/CD pipelines, to strengthen security posture and ongoing evaluation.
Pre-defined Policies
It provides predefined PCI, SOX, and other compliance, data regulatory, and data governance rules.
Advanced Monitoring Equipment
Obtain access to Database Monitoring tools such as DML, DDL, and DCL for logging SQL transactions. This is possible without using local database logs.
Access Authorization & Administration
Ensures that the service account will have database access from the specified IP source. This assists in spotting breaches of a service account that often originate from the system.
Boost the threat management lifecycle by integrating modern cloud-based technologies, such as threat investigation, deep hunting, threat analysis, vulnerability assessment, and threat remediation.
CDWT DevSecOps and SecOps End-to-End Solutions and Services
- Automated Code Analysis and Code Scanning
- Change Management
- Compliance Monitoring
- Investigating Threats
It expedites the detection of flaws and vulnerabilities by delivering and assessing software and application code in tiny pieces or fragments on a recurring basis.
It allows users to contribute improvements that may increase productivity and velocity. It is also crucial in assisting security teams in determining the effect of changes. Deploy Secops Team's security tools and technologies to uncover vulnerabilities and boost security in modified areas.
Compliance is a crucial indicator for maintaining process security. All businesses must comply with requirements such as the General Data Protection Regulation (GDPR) and the Payment Card Industry Digital Security Standard (PCI DSS) and be ready for audits at any moment. CDWT provides comprehensive compliance audits, assessments, and framework implementations that adhere to local, national, and international laws.
Each programming update introduces vulnerabilities to rising threats. It is of the highest significance to detect these risks or vulnerabilities at an early stage and to develop appropriate solutions for threat mediation.
- Vulnerability Assessment
- CI/CD Security
- Quality Monitoring
- Enterprise Risk Assessment
- Security Automation Integration
Identify key vulnerabilities and malevolent flaws by evaluating user IDs, user controls, workloads, accounts and access rules, and user conduct. Analyze gathered data to forecast future risks and IT health failures. Threat intelligence delivers actionable insights derived from examined data for better vulnerability management. Manage security activities in response to evolving risks.
Central to a productive and efficient DevOps system are CI/CD (Continuous Integration/Continuous Delivery) pipelines. These tools and technologies automate the steps of code development, deployment, and testing. SecOps frameworks and technologies enhance the security of CI/CD systems inside the development and operations processes.
Obtain improvement and consistency with a complete picture of the infrastructure security. Continuously monitor for detection, investigation, hunting, and analysis of threats. Advanced threat intelligence is used to ensure risk-proof code and systems with great efficiency.
Assessment and analysis of security risks from all angles, aiding in the early discovery of vulnerabilities and threats. Continuous risk evaluation of assets include corporate systems, platforms, software, applications, and interconnecting networks, among other components. Minimize data loss and security risks, including application development security concerns.
Deploy development and operations processes using sophisticated security automation solutions and platforms such as Security Incident and Event Management (SIEM), Security Orchestration Automation and Response (SOAR), Managed Detection and Response (MDR), and others. Enhance security by design and conduct ongoing audits and analyses of latent risks and weaknesses.
Frequently, SecOps tools and solutions are coupled with asset data and dataflows to provide instantaneous risk and vulnerability assessments. Maintain data security and integrity with ease.
Collaboration across development, operations, and security workflows facilitates the optimization of duplicate procedures, dangerous gaps, and vulnerabilities. Deploy highly secure and high-performance solutions to reduce security-related losses and enhance IT return on investment over the long term.
The gap between the security team and the IT software developers must be bridged by businesses. This may be accomplished with sufficient security training and a comprehensive set of standards.
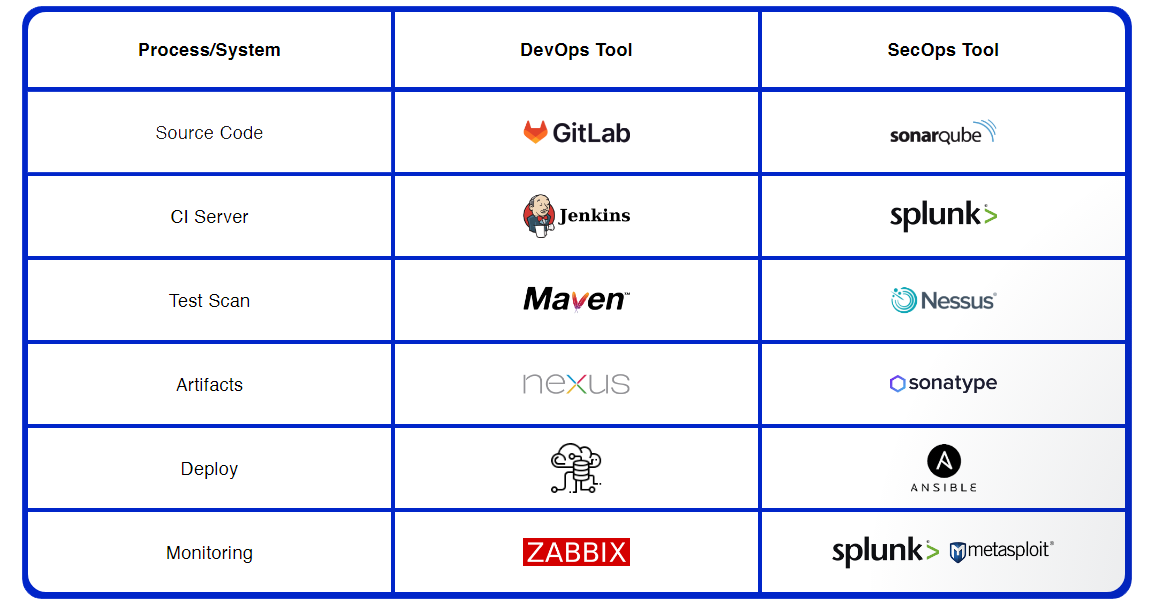
SecOps Solutions and Tools