Application Security Services & Solutions
Monitor application codebases, libraries, source code files. Protect runtime applications against external dangers and malicious invasions. Protect related infrastructure with superior intelligent cybersecurity and cutting-edge testing and application security technologies.

Enterprise Application Security: Protecting the Heart of Daily Operations and the On-Premises and Web Applications that Power Them
Apps. One term that describes our everyday smartphone digital encounters. Without mobile applications, the intelligent handheld gadget would be a black box with no apparent value. Similarly, we seldom recognize that the business apps used by thousands of people from a variety of departments are the fundamental structures driving the digital transformation goal of a company. Whether Supply Chain Management, Human Resource Management, Enterprise Resource Planning (ERP), Customer Relationship Management (CRM), or other enterprise applications, the adoption of SaaS or on-premise models has a direct impact on an organization’s operational efficiency, ROI, and future relevance.
Consequently, application security management is of paramount relevance for businesses of all sizes and industries today. CDWT, the world’s largest application-focused managed cloud services provider and a leader in cybersecurity, provides end-to-end security solutions and services to protect application codebases, source code files, development environments, runtime ecosystems, underlying backend infra, servers, VMs, and networks, among other things. Open web application security best practises for enhanced software composition analysis and vulnerability assessment across software development lifecycles. Incorporate a DevSecOps culture with CI/CD pipelines and Application Security Testing, assess vulnerabilities 24×7, integrate threat intelligence and user behaviour analytics with entire app data feeds and telemetry, adopt cloud-based app monitoring and security tools, deploy and manage network firewalls, streamline VMs and endpoint security, and adopt advanced managed detection and response for end-to-end protection. Without sacrificing security and continuity, unleash hyper-application performance.
Advantages of Implementing Specialized On-Premise and Web Application Security Services and Solutions
In-depth analyses of existing app cybersecurity postures, company goals, and the development of a tailored application security strategy blueprint.
24/7 monitoring, hunting, and analysis of all application management and development environments
Protect application perimeters via network firewalls, VPNs, and other network intrusion prevention technologies.
Conduct real-time security testing on codebases, source code files, libraries, CI/CD pipelines, and development environments.
Conduct penetration testing and real-time security monitoring throughout application runtimes. Advanced security is achieved by simulating the worst possible cyberattacks on the targeted application.
Integrate enhanced threat intelligence into business applications. Connect the same to app telemetry, data streams, and third-party connections in order to forecast threats and their behaviors, processes, and tools.
Analyze the user habits of an application and filter out questionable activity. Protect application endpoints with sophisticated threat detection and response
Protect application environments end-to-end with sophisticated security automation solutions such as Managed Detection and Response, SIEM-SOAR, IAM, PAM, Security vulnerability Assessments, and Penetration Testing, etc.
Enhance cloud application deployment and security with the ideal combination of cloud security technologies and cloud management services.
Connected hosted assets such as emails, software development landscapes, operating systems, middleware, servers, datacenters, VMs, and networks are secured using cutting-edge tools, technologies, and protocols.
Ensure application processes are compliant with data residency laws, national and international requirements, and best practises.
Implement a highly efficient and cost-effective SecOps and DevSecOps methodology. Implementing Security by Design may reduce total application development and application management security expenses.
CDWT Complete On-premises and Web Application Security services and solutions
- Application Security Evaluation
- DevSecOps & SecOps
- Web Application Protection
- Automated Code Analysis and Code Scanning
- Change Management
- Compliance Monitoring
Execute strategic evaluations to identify critical security vulnerabilities in the present application management and development environments. Hunt for latent threats and vulnerabilities on runtime applications (self-protection), as well as identify compliance disruptions and questionable processes. Using interactive application security solutions and web application firewalls, develop a security plan adapted to the operations of the enterprise.
Integrate security by design into your application management processes, development procedures, and workflows. Utilize application security testing and security automation solutions throughout code development, testing, deployment, and operation. Optimize operating and development expenses by enhancing app security from inside outwards.
Protect all company online applications and their associated resources, such as hosted email, user accounts, confidential data, etc. Audit and monitor all web application assets and user processes in order to identify suspicious activities. Easily secure application endpoints.
It expedites the detection of flaws and vulnerabilities by delivering and assessing software and application code in tiny pieces or fragments on a recurring basis. Utilize specialist evaluations for penetration testing.
This allows users to contribute modifications that may improve efficiency and speed. In addition, it plays a significant role in assisting security teams in determining the effect of modifications on codes, CI/CD pipelines, implemented solutions, etc. Deploy security tools and technologies to uncover vulnerabilities and strengthen the security of the modified components.
Compliance is a crucial indicator for maintaining process security. All businesses must comply with requirements such as the General Data Protection Regulation (GDPR) and the Payment Card Industry Digital Security Standard (PCI DSS) and be ready for audits at any moment. CDWT provides comprehensive compliance audits, assessments, and framework implementations that adhere to local, national, and international laws.
- Secrets and Keys Administration
- Vulnerability Assessment
- Essential Application Security Testing Services and Solutions
- Quality Assurance
- Identity and Access Management for Applications
- Integrity of Data and Analytics
Protect all secrets and sensitive data contained in CI/CD systems, including Keys, APIs, login IDs and passwords, authentication, and User access restrictions. If necessary, disperse data across numerous secure vaults and update them on a regular basis for optimum protection.
This requires a thorough evaluation and analysis of unidentified threats and new vulnerabilities. To mitigate future risks and threats, analyse possible vulnerabilities across all source code, libraries, development platforms and environments, containers, systems or virtual machines executing development processes, and more.
Central to a productive and efficient DevOps environment are automated app development procedures and capabilities. These tools and technologies automate the steps of code development, deployment, and testing. Consequently, frequent security reviews are required. SAST or Static Application Security Testing performs continuous threat monitoring and auditing on software, applications, etc. in development. DAST, or Dynamic Application Security Testing, offers improved monitoring and risk evaluations for applications and software that are actively operating or in use by various organizational divisions.
Achieve consistency and improvement with a holistic picture of security infrastructure across all codebases, storages, platforms, libraries, CI/CD pipelines, and more. Continuously monitor for detection, investigation, hunting, and analysis of threats. Ensure code and systems are risk-free and highly efficient.
Based on their duties, share roles, authentication, and platform access control with users. Identity and Access Management facilitates the management of identities, the analysis of user behaviour, and the protection of systems and applications against leaks and suspicious activity.
Frequently, security tools and solutions are coupled with asset data and dataflows to provide immediate risk and vulnerability assessments. Maintain data security and integrity with ease. Compile threat monitoring and historical data from application environments and CI/CD solutions in order to acquire a thorough knowledge of the behaviour of threats, followed by the formulation of action plans.
- Integration of Security Event Management and Security Automation
- Security of Application Infrastructure (Networks, Servers, Datacenters)
- Asset Protection (OS, Middleware, Hosted Assets)
- Application Cloud Security
- Mitigate Security Issues by Optimizing Processes
- Training
Deploy sophisticated security automation solutions and platforms to development and operational processes, such as Security Incident and Event Management (SIEM), Security Orchestration Automation and Response (SOAR), Managed Detection and Response (MDR), and others. Strengthen security by design and conduct ongoing audits and evaluations of latent risks and vulnerabilities. Let all security management procedures be automated within the context of a CI/CD environment.
Strengthen underlying assets that are tied to corporate applications. Incorporate specialized security solutions monitoring application networks, servers, VMs, datacenter assets, and dataflows for sophisticated threat analysis. Easily detect latent threats, improve network security, minimize application vulnerabilities and dangerous malware, and thwart premeditated assaults. Even during development, protect important data against unknown attack vectors.
Protect application assets, including operating systems, middleware, runtime environments, hosted emails and their secrets, and more. A comprehensive application security policy must safeguard the application's processes and the underlying assets used to execute the apps. Utilize a Zero Trust Security strategy.
Deploy the optimal combination of cloud-native threat monitoring, auditing, IAM, keys management, incident management, response orchestration, and threat intelligence tools to protect cloud application structures, modules, workflows, and assets. Deploy sophisticated cloud application security across public-private-hybrid-multicloud architectures powered by GCP, AWS, Azure, IBM Cloud, OCI, and others.
With application management, development, operations, and security workflows collaborating, duplicate procedures, hazardous gaps, and vulnerabilities may be efficiently optimised. Deploy highly secure and high-performing technologies to reduce security-related losses and hence enhance IT ROI over time.
Companies must bridge the divide between their security staff and their IT software developers. This may be attained by proper security-related training supported by a comprehensive set of recommendations. The management of CI/CD pipelines is simplified with the right level of understanding.
Application DevSecOps Solutions and Tools
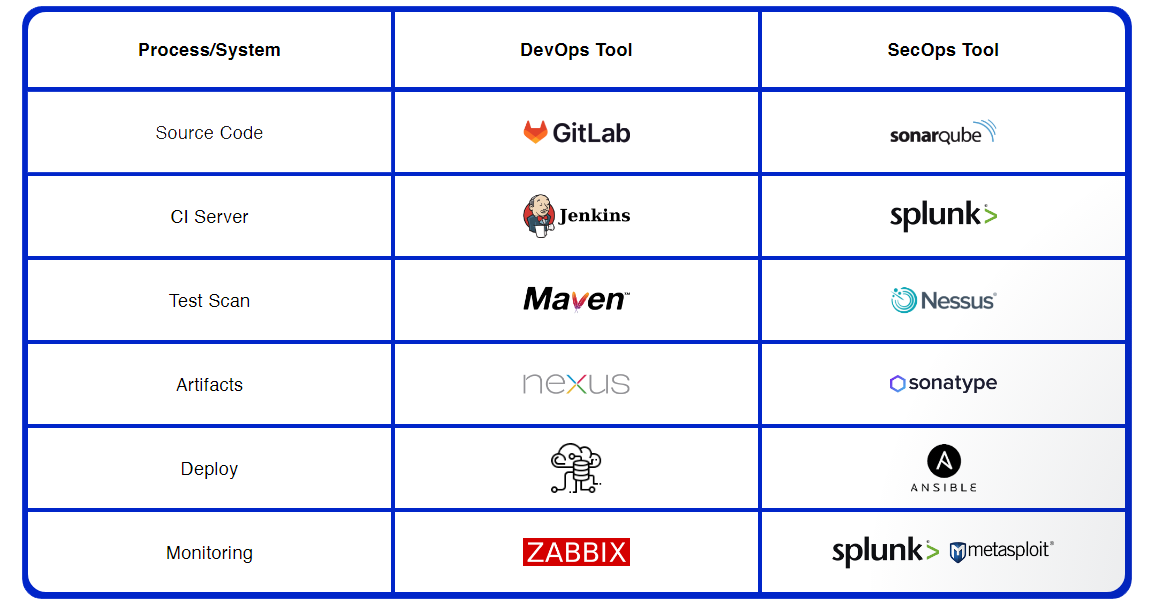
Cloud Application DevSecOps Landscape






