Cybersecurity Management using CDWT on GCP: A Fault-Proof Plan for a Resilient and Intelligent Enterprise Future
Globally, 93% of businesses are worried about cybersecurity risks.
The event occurred around a year ago. Sundar Pichai, the CEO of Google and Alphabet (Google’s parent company), spoke out on the need for AI Ethics and AI Regulations, a daring move from a firm at the forefront of the global AI revolution. However, upon closer inspection, the feeling may be linked to the proliferation of AI’s cybersecurity applications. Similar to the arms race of a century ago, institutions (both public and commercial) must cooperate and progress the development of compliant, well-regulated sophisticated AI technologies before cybercriminals achieve the reverse. Data is the new oil and the cause of our contemporary global conflict. And, as illustrated in the preceding statistic, the majority of businesses are on the receiving end of this struggle between IT titans and cybercriminals.
This necessitates the rapid global adoption of modern, intelligent cybersecurity solutions, and cloud security may be the answer. Leading cloud providers like Google Cloud Platform (GCP) have invested billions to strengthen enterprise security end-to-end: backend IT infrastructure, computing devices, network, storage, and data, workloads and workflows, datacenters, software platforms and architectures, business applications, g suite solutions, edge and endpoint networks, IoT environments, etc. In order to assist the implementation of these cloud security developments, managed security vendors such as CDWT have become the crucial link between cloud providers and end businesses.
CDWT, as the world's leading application-focused managed cloud service provider with worldwide experience in cloud cybersecurity management, is positioned to be the right partner for securing IT on Google cloud. Using best security practises, shield assets end-to-end with enhanced automation and cloud-native security solutions, data encryption keys, intelligent threat prevention, compliant-ready cloud architectures, and 24/7 managed SOC support on GCP. Responsibility. Resilience. Revolution.
Cybersecurity on Azure Cloud: Maximum Protection and Return on Investment
- Transparency and Managed Service
- Environment Complicatedness
- System Dependability
- Costs Management
- Compliance
- Resource Management
- Incident Management
- Access Management
- Obsolete Policies
- Monitoring and Protection of Assets
- Support and Administration
- AI Capabilities
Scale operations safely with enhanced visibility and control on Google Cloud. Gain risk management insight over your IaaS, PaaS, SaaS, and CaaS environments with centralised GCP managed cybersecurity services or GCP cybersecurity-as-a-service. Utilize automatic warnings for internal-external threats. Utilize the Cloud Console for end-to-end management and monitoring of assets and applications, the Cloud Armor for security policies and protection against cyber threats, and the Security Command Center to acquire a full platform to defend/protect Google Cloud Assets. Utilize Cloud Identity to manage, monitor, and protect user devices and apps globally.
Access versatile, highly scalable, and agile security platforms and solutions on Google Cloud Platform that are adaptable to any IT environment or resources, software, backend, workload, apps, networks, edge and IoT settings, and more. Utilize Access Transparency, Chronicle, Cloud Key Management, Cloud Asset Inventory, Cloud Data Loss Prevention, Firewalls, Google Cloud Audit Logging, StackDriver, Google IAM Recommender, Shielded VMs, VPC Service Controls, Network Telemetry, Cloud Armor, Apigee API Management, Cloud Console, Network Intelligence Center, Kubernetes Monitoring, Cloud Identity, Policy Intelligence, Chronicle, Web Risk, Titan Security Key, Cloud Identity, IAM,
On the Google Cloud Platform, powerful information security and computing technologies may be integrated for unparalleled dependability. Adhere to current security frameworks and procedures to easily safeguard your organisation. Streamline access management across all resources with Access Transparency and Binary Authorization, elastic and telemetry security with Chronicle, monitor assets with Cloud Asset Inventory, prevent data risks with Cloud Data Loss Prevention, manage data and key encryption with Cloud Key Management and Confidential Computing, protect sensitive information with VPC Service Controls, administer firewalls with Firewalls manager, Identity Management with Secrets Manager and Firewalls manager, and administer firewalls with Firewalls manager.
Eliminate the need for specialised hardware and IT infrastructure to process security and risk management inquiries. With all IT assets safeguarded on the Google cloud, you can decrease administrative costs and pay just for what you need. Using GCP Cost Management Tools, continually audit GCP resources to optimise future compliance, risk assessment errors, and costs. Google Cloud Platform offers automatic, rapid, and cost-effective disaster recovery
Google's cloud security architecture is compliant and includes local, national, and international compliance-regulatory requirements. Adopt security architectures that are compliant-ready and empowered with continuous compliance monitoring and auditing. Utilize Policy Intelligence to achieve intelligent access control management, better comprehend and administer policies, and incorporate essential automation technologies. Sole-tenant Nodes are hardware devoted to compliance, licencing, and administration. For critical workloads, use Assured Workloads for compliance and security controls. Utilize Binary Authorization to deploy on the Kubernetes Engine only trustworthy containers and security rules depending on requirements.
Google cloud security services and solutions that automate continuous monitoring, proactive maintenance, and risk alerts eliminate the requirement for dedicated manhours. Easily administer worldwide corporate security with little human involvement required for duplicate duties. Explore options like Cloud Console, Network Intelligence Center, Network Telemetry, Cloud Asset Inventory, and Assured Workloads, among others.
Reduce mean time to detection and mean time to repair by a significant margin with Advanced Managed Detection and Response on Google Cloud. Integrate AI-enabled enhanced threat hunting and automated reaction management. Acquire a comprehensive incident analysis for data-enhanced security decision-making. Discover, examine, encrypt, and safeguard sensitive data with Cloud Data Loss Prevention, Cloud Key Management, Confidential Computing, and Secret Manager, among others. Adopt Shielded Virtual Machines, which have extensive security protections. Utilize Chronicle to monitor assets and immediately detect threats. Rapid, automatic Disaster Recovery is available.
GCP makes it simple to evaluate security and architectural access roles for the whole company. Utilize the user-friendly GCP Incident and Access Management (IAM) and Privileged User Access Management (PAM) to assign specific roles and manage capabilities throughout the security processes. Gain access control and visibility with Access Transparency, Assured Workloads, and so on. Circumstances-aware Access manages access to programmes and infrastructure depending on user identification and context. Implement Zero Trust Model of Security. Manage Identity and Access in the cloud using Cloud Identity, Identity Platform, Identity-aware Proxy, and Google IAM, among others.
Replace obsolete cybersecurity policies. Embrace world-class approaches, technologies, and frameworks, such as SIEM-SOAR, MITRE ATT&CK, CIS Security Controls, and Zero Trust, for protecting IT assets in the Google cloud. Utilize powerful GCP native security technologies and solutions, including Chronicle, Binary Authorization, Apigee API Management, Firewalls, Secret Manager, Cloud Data Loss Prevention, Web Risks, Cloud Asset Inventory, and Cloud Key Management.
On Google Cloud Platform, you can monitor your devices, data, networks, platforms, apps, VMs or virtual systems, and servers around-the-clock. Obtain unmatched security throughout your whole backend and endpoint infrastructures. Track assets with embedded alerts, AM-ML-Behaviour Analytics, and cloud-native cybersecurity solutions such as Cloud Console, Network Intelligence Center, Network Telemetry, Cloud Asset Inventory, Assured Workloads, Kubernetes Engine Monitoring, Firewalls, and more.
The Google Cloud Security Operations Centre (SOC) team monitors, manages, and governs your cybersecurity monitoring, management, and governance concerns around-the-clock. GCP provides access to one of the biggest ecosystems of security partners and solutions. Utilize the Google Security Command Center to protect all GCP assets and the Risk Protection Program to receive access to a unique cybersecurity management and insurance programme.
24/7, the Google Cloud Security Operations Centre (SOC) staff handles your cybersecurity monitoring, management, and governance issues. GCP offers one of the most extensive ecosystems of security partners and solutions. Utilize the Google Security Command Center for protecting all GCP assets and the Risk Protection Program in order to have access to an unique cybersecurity management and insurance programme.
A Shared Responsibility Model for CDWT Cybersecurity Management on GCP
Contrary to common opinion, organisational security management is based on a principle of shared responsibility. While managed cybersecurity providers like as CDWT track, monitor, and secure all cloud infrastructure and corporate assets, businesses must be mindful of their privately managed data points, cloud-based processes, on-premises activities, inherent IT controls, and business choices. Any error in the latter might have devastating consequences for businesses and their end consumers.
- Client Responsibility
- GCP and CDWT Responsibility
| Client Responsibility | GCP and CDWT Responsibility | |
| IaaS Security | ->Content ->Access policies ->Usage ->Deployment ->Web application security ->Identity ->Operations ->Access & authentications ->Network security | ->Guest OS, data & content ->Audit logging ->Network ->Storage + encryption ->Hardened Kernel + IPC ->Boot ->Hardware |
| PaaS Security | ->Content ->Access policies ->Usage ->Deployment ->Web application | ->Identity ->Operations ->Access & authentications ->Network security ->Guest OS, data & content ->Audit logging ->Network ->Storage + encryption ->Hardened Kernel + IPC ->Boot ->Hardware |
| SaaS Security | ->Content ->Access policies ->Usage | ->Identity ->Web application Identity ->Operations ->Access & authentications ->Network security ->Guest OS, data & content ->Audit logging ->Network ->Storage + encryption ->Hardened Kernel + IPC ->Boot ->Hardware |
GCP Workload End-to-End Security Management
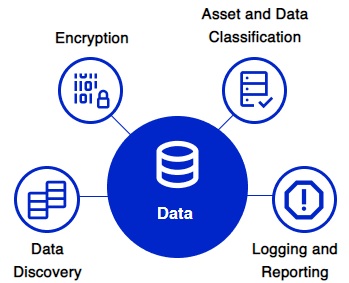

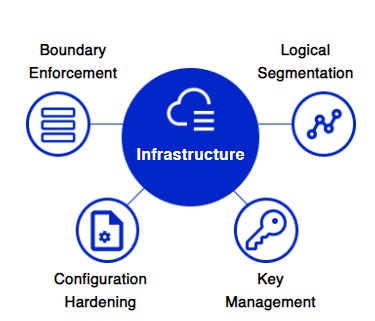

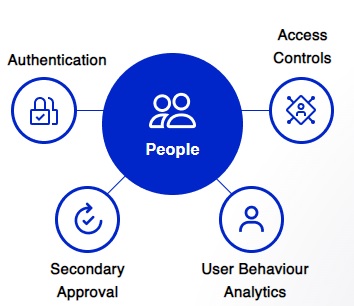

In Brief: CDWT Managed GCP Security Services End-to-End
CDWT, the world’s largest application-focused cloud managed services provider and a leader in managed cybersecurity, has spent years developing a futuristic, highly intelligent end-to-end managed cybersecurity services and solutions portfolio for your assets: devices, networks, servers, applications, systems, workloads, virtual systems, and most importantly data. Advanced Google cloud security services capabilities and solutions provide comprehensive protection for your enterprise IT assets, including networks, data centres, dataflows, workloads and traffic load balancing, computing devices, email assets and applications, adopted technology and storage solutions, software, platforms, applications, edge networks, and IoT environments in the cloud.
Leverage the greatest security and cybersecurity-as-a-service products on the market by using completely compliant, automated, and AI-driven platforms powered by Google's cloud. Integrate unique threat management frameworks and get maximum cloud security advantages with GCP at little expense. Access Transparency, Chronicle, Cloud Key Management, Cloud Asset Inventory, Cloud Data Loss Prevention, Cloud Key Management, Firewalls, Google Cloud Audit Logging, StackDriver, Google IAM Recommendation, Shielded VMs, VPC Service Controls, Network Telemetry, Cloud Armor, Apigee API Management, Cloud Console, Network Intelligence Center, Kubernetes Monitoring, Cloud Identity, and Policy Intelligence.
Obtain 24/7 automated monitoring, predictive alerts, and in-depth cybersecurity analytics, as well as consultation and support services. CDWT's AI-driven Managed Detection and Response (MDR) and Security Operations Centre (SOC) products on Google Cloud will enable you to implement cutting-edge cybersecurity approaches and frameworks throughout your entire security strategy. CDWT managed cybersecurity services provide uncompromising security, continuous continuity, and unstoppable transformational development. Deliver an uninterrupted service experience to end users and customers.
- End-to-end Infra Security with Managed Cybersecurity-as-a-Service from Google Cloud Platform
- MDR on GCP with Advanced Managed Detection and Response
- Managed GCP Security Operations Center (SOC) Services
- GCP Security for IaaS
- GCP Security for PaaS
Google cloud offers end-to-end managed cybersecurity services or cybersecurity as a service. CDWT offers full cloud security strategy, design, proof-of-concept, and implementation services, as well as hybrid multi-cloud security management. On GCP, your enterprise’s IT assets, including networks, data centres, dataflows, workloads, computing devices, storage solutions, software, platforms, applications, edge networks, and IoT environments, are completely protected.
Explore individualised needs and solutions for monitoring and securing assets, virtualization security, authentication and access control management, data categorization and segmentation, configuration hardening, key management, and more. Streamline access management across all resources with Access Transparency – Assured Workloads and Cloud Identity & Access Management; elastic and telemetry security with Chronicle; monitor assets with Cloud Asset Inventory and Cloud Console; prevent data risks with Cloud Data Loss Prevention; manage data and key encryption with Cloud Key Management and Confidential Computing; safeguard sensitive data with VPC Service Controls; and administer firewalls with Firewalls ma. Obtain GCP cybersecurity advice and help around-the-clock. Enhance asset DR management with Google Cloud’s rapid, automated solution.
CDWT’s advanced Managed Detection and Response solution and services on Google Cloud Platform provide 360-degree protection, intelligent 24/7 real-time monitoring, threat hunting/risk prediction alerts, threat detection, and risk mediation. Gain deeper vigilance of your infra assets including data, networks, workloads, traffic, devices with ease and enjoy end-to-end reaction management: Threat and Mal Containment, Incident Analysis, Data Exploration, Response Orchestration. Protect your endpoint connection with Google Cloud’s End-Point Protection and Response Platform, which is driven by artificial intelligence. Utilize the Cloud Console for end-to-end management and monitoring of assets and applications, the Cloud Armor for security policies and protection against cyber threats, and the Security Command Center to acquire a full platform to defend/protect Google Cloud Assets. Use Cloud Identity to manage, monitor, and protect user devices and apps globally.
Having an in-house, dedicated monitoring and response staff for cybersecurity services might be quite costly for any firm. This not only discourages cyber threat monitoring, detection, and remediation, but also hinders the organization’s ability to implement sophisticated security solutions and services. As a supplier of GCP-managed SOC (Security Operations Center) services, Cloud4C functions as an extended Cybersecurity Incident and Response Team (CSIRT) for your Google cloud security management. The agreement simplifies all monitoring and threat management tasks and facilitates the use of innovative cybersecurity frameworks, methods, and intelligent solutions supported by the Google cloud. Utilize the Google Security Command Center to protect all GCP assets and the Risk Protection Program to receive access to a unique cybersecurity management and insurance programme.
Modernizing backend architecture has a significant impact on enhancing frontend experiences. However, maintaining the security of all IaaS solutions, including virtual networks, computing, storage, and more, is crucial for ensuring uninterrupted company operations. Shift and protect your networks, datacenter assets, including databases, computing, storage, and servers infrastructural components, to Google cloud solutions that are devoted to your needs. Utilize Google cloud-native apps and implement a virtualized GCP architecture with Shielded VMs to achieve exceptional agility and scalability of corporate applications without sacrificing asset protection. Eliminate all backend physical infrastructure issues and just pay for what is consumed.
With businesses increasingly choosing for complicated, multi-hybrid, private cloud IT architectures, application universality is compromised. Frequently, businesses fall victim to isolated systems and apps that perform fine for one backend platform or vertical but are incompatible with another cloud environment used for a different vertical. This results in non-synchronized operations and hence catastrophic risk possibilities, which might be mitigated with a secure, pay-per-use GCP PaaS platform. In addition to virtualizing and modernising all core infrastructure assets on the cloud, migrate middleware, OS, architectures, protocols, APIs, libraries, Microservice modules, and containers (Streamline Container Security with Binary Authorization) to GCP with the highest level of protection and zero disruptions. Leverage current cloud-native platforms and GCP security frameworks to design, deploy, and execute applications in any IT environment, anywhere, with the highest level of protection.
- Application & SaaS Security on GCP
- CaaS Security on GCP
- Storage & Data Security on GCP
- Network Security on GCP
- Hybrid & MultiCloud Security on GCP
Adoption of web apps or GCP SaaS applications has become the standard in order to protect businesses from the many difficulties and hazards associated with application creation, maintenance, administration, and resulting data management. Easily evaluate application software codes, backend logic, architectures, and user interface vulnerabilities using Google cloud security solutions. CDWT assists clients in navigating modern GCP security services and solutions and embracing secured, compliant-ready SaaS corporate applications that best meet their present and future requirements. CDWT manages the full application lifetime in terms of maintenance, security, updates, and asset management, while the client easily reaps the functional advantages. Utilize Web Risks to protect web apps from harmful activity, Apigee API Management for safe application development, and Secret Manager and VPC Controls to protect important app data.
Cloud-based application modernisation has altered company operations across several industries, including CRM, workflow management, supply chain management, compliance checks, financial audits, productions and manufacturing, and IT administration. Modern application development technologies, such as microservices, containers, and functions, are essential for achieving the same goal and monitoring applications and databases across diverse IT environments with ease. Gain cutting-edge protection over Docker or Kubernetes containers, optimise development workflow security, architectural scanning, and access restrictions, and more with CaaS security on GCP. Utilize Binary Authorization to deploy only trusted containers on Kubernetes Engine, along with policy formulation based on security requirements, audit logging, policy verification and enforcement.
CDWT delivers military-grade data security during migration by implementing end-to-end pre-backup, secure data transmission, end-to-end encryption, data integrity management, exhaustive testing, vulnerability assessment, and appropriate access control capabilities. Add additional security levels to your GCP Storage solutions, such as files, blocks, objects, databases, and database management tools. Using Cloud Console and Cloud Asset Inventory to track assets, Manage access levels with Access Transparency and Context-aware Access, sensitive data inspection and administration with Cloud Data Loss Prevention, Data and key encryption with Cloud Key Management and Confidential Computing, and Secrets Manager to store hyper-sensitive data such as passwords, keys, etc. in a secure environment. Utilize cloud-native monitoring and identity and access management systems, such as GCP IAM, Cloud Identity, etc., that are available 24/7. Incorporate threat information and advance your ability to detect and avert dangers even before they materialise. Adopt innovative preventative maintenance capabilities (Self-Healing Operations).
The complexity of organisational networks and communication infrastructure has grown significantly over time. Rapid digitalization has enabled organisations to rapidly scale up operations, integrate diverse systems and IT solutions, decentralise processes across multiple locations, develop private network architectures to remain connected 24 hours a day, seven days a week, and deploy global remote workforces. Obviously, network assets are the basis of such a corporate labyrinth, allowing businesses to function each day without interruption. Therefore, it is imperative that IT systems, processes, corporate applications, online assets, and more get real-time network security attention. Network Intelligence Center allows for the intelligent monitoring, verification, and optimization of networks. Network Telemetry enables the management of VPC Flow logs for network monitoring, forensics, and security.
The use of hybrid and multicloud systems is accelerating as a result of distinct advantages, the adaptability of IT adoptions, and other factors. Protect your GCP Anthos architecture with cloud-native solutions of the highest calibre. Gain the advantages of on-premises dependability and GCP-level security. Transfer security and monitoring checks across private and public workloads, touchpoints, and assets in a dependable manner. Comply with data locality-residency laws, achieve ultra-low latency, and enjoy continuous, consistent performance of hosted workloads, applications, and systems while maintaining the highest level of security. Utilize Apigee API Management for safe API development and administration, Cloud Build for conducting secure constructions on Google Cloud Infrastructure, and Looker Platform for secure BI and integrated Data Analytics management.
Self Healing Operations Platform (SHOP) for GCP: Automated Intelligent Operations, Predictive and Preventive Healing
CDWT SHOP is a low-code AI-powered platform that unifies the many tools and solutions required to offer enterprise-level managed cloud services. The intelligent platform integrates hundreds of operational platforms and applications, such as auto-remediation and self-healing, into a single system. This allows the whole infrastructure and application landscape to be automatically controlled through a single pane of glass, while giving clients with a comprehensive picture of their IT infrastructures. The platform increases the productivity of engineers and enables less-experienced engineers to undertake more complicated jobs, while guaranteeing a six-month concept-to-delivery window.
SHOP positions CDWT as the leading Application-focused Managed Services provider in the world with stringent security administration expertise.
Remedial & Independent
Anticipatory & Preventive
Collective Understanding
Situational Consciousness
Intelligent, Automated Management of Operations
Custom Automation solutions for Google Cloud
CDWT’s automation solutions streamline Google cloud security management for your operations and unleash failsafe innovations. Utilize AI managed by CDWT’s elite Site Reliability and Security Engineers for n-tier design, heterogeneous systems management, and numerous frontends, backends, and middleware for caching, searching, and queuing relational and non-relational databases. CDWT automation solutions for GCP-managed security operations aid in continuous monitoring of data platforms and applications, proactive risk management alerts, maximising availability, and self-healing.
CDWT Cloud Management Tool
CSP Portal
CMDB
Automate. Administer. Advance: CDWT Google Cloud Security Adoption Framework
DIRECTIVE
- Azure Account Governance
- GRC Control Framework
- Data Classification
- Change and Asset Management
- IAM and Least Privilege Access
- Security Operations Playbook and Runbooks
PREVENTIVE
- Identity and Access
- Infrastructure Protection
- Data Protection
DETECTIVE
- Logging and Monitoring
- Security Testing
- Asset Inventory
- Change Detection
RESPONSIVE
- Incident Response
- Security Incident Response Simulations
- Forensics
LEVEL 01
- Monitoring
- Open Tickets
- Investigation and Mitigation
- Addressing False Positives
- Automated Policies for Actions
LEVEL 02
- Deep Investigation/CSIRT
- Automated/Manual
- Mitigation
- Recommended Changes
- Reporting
LEVEL 03
- Advanced Investigation/CSIRT
- Business Threat Hunting & Prevention
- Forensics
- Counter Intelligence
- Identity and Theft Protection




