Advanced Threat Protection (ATP)
Defend your enterprise’s IT perimeters and internal landscapes against sophisticated, unanticipated, and changing cyberthreats. Explore unique threat intelligence and apply proactive incident detection, response, and cleanup solutions
Unlocking Defense-in-Depth: A Protection That Exceeds Conventional Methods
As cyberattackers and their tactics get more complicated and sophisticated, it is necessary for businesses to develop and prepare for future risks that might inflict permanent harm. With technical developments and security changes, businesses are often prepared for rule-based attack vectors or incursions that are borderline deep. However, the closeness of easily accessible data repositories and the explosive growth of creative technology have enabled thieves to undertake unprecedentedly infamous and almost undetected assaults against targeted businesses.
Organizations must implement solutions like as advanced threats management, zero-day protection, anti-phishing policies, exchange online protection, and more in order to shield themselves against such evolving attacks and recover fast from any security events. The lack of trained resources to identify, decode, and react to such sophisticated malicious activities is, nevertheless, one of the greatest obstacles faced by businesses in the face of such serious assaults. Cybersecurity executives are thus searching for dependable partners that can implement creative, updated data protection techniques, assemble devoted extended security teams, and integrate cutting-edge technology to alleviate enterprises’ ongoing threat anxiety. Must-haves include proactive monitoring, fast finding and detection, and automated reaction and cleanup.
CDWT's Enhanced Threat Protection: is Powered by Advanced SOC Practices
CDWT is renowned for its worldwide advanced cybersecurity standards, cloud-native security experience, and proficiency in providing comprehensive cyber defence solutions.
With CDWT’s Advanced Threat Protection, businesses can protect their sensitive databases, IPs and hosted assets, accounts, networks, platforms, and applications from deep-targeted hacks, intrusions that do not conform to existing patterns, advanced malware and ransomware, and sophisticated phishing attacks. Construct a one-of-a-kind cyber defence system supported by sophisticated threat intelligence, AI-powered security solutions, and a world-class SOC staff operating as your extended partner for all of your cybersecurity requirements 24 hours a day, 7 days a week. In addition to typical anti-threat software and techniques, Advanced Threat Protection provides your IT operations with a much-required, much-deeper, and much-smarter shield, headed by a trusted and inventive cybersecurity team.
Why Should: Your Enterprise Include Advanced Threat Protection in Its Cybersecurity Arsenal?
Implement specialised cybersecurity software to guard against sophisticated cyberattacks and threats.
Advanced monitoring for malicious activity, suspicious footprints, and possible susceptibilities or vulnerabilities to threats.
Gain maximal cloud security advantages at lowest expense and incorporate innovative frameworks for threat management.
Identify hazards or breaches accurately to reduce false positives and alert fatigue among cybersecurity professionals.
Continuous identification and correction of landscape misconfigurations.
Intelligent prioritising of security events based on operational and commercial requirements.
Coordination of vulnerabilities with endpoint ecosystems to provide end-to-end protection.
Deploy sophisticated machine learning tools to explore and search for risks, breaches, and threat trends.
Built-in repair methods by integrating powerful Microsoft technology and other world-class solutions in a novel manner.
Seamless integration with specialised threat management systems, including SIEM, SOAR, and XDR.
Utilize sophisticated threat information to map threat behaviours, processes, and policies for enhanced security.
Integration with cloud-native solutions and cybersecurity systems like Azure Sentinel.
Enable Zero Trust Security principles across the whole company environment, including remote ecosystems.
Integrate and deploy proprietary security automation technology
High Level Snapshot: What Are Examples of Advanced Threats?
Advanced Malware and Ransomware
Rootkits, Trojans
Automated Phishing Tools
Crypto Mining Malware
Advanced Persistent Threat (APT)
Cloud Jacking
Zero Day Attacks
DDoS Attacks
CDWT Advanced Threat Protection:
Integration of World-Class Security Services and Solutions
Microsoft Defender Advanced Threat Protection
- Attack Surface Decrease
- Detection and Reaction at the Endpoint
- Automated Investigation and Remediation
- Risk and Vulnerability Administration
-
Office 365 Advanced Threat Protection
- Email and Attachment Security
- Shareable Links Security
- Imitate Intelligence
- Superior anti-phishing capacities
-
Advanced MDR and EDR Solutions
- Threat Targeting
- Intrusion Management
- Database Monitoring of Activity
- Superior Threat Detection and Reaction
-
Advanced Threat Analytics
- Behavioural Analysis
- Data Forensics
- Superior Threat Intelligence
- Threat Strategies, Conduct, Procedures, and Security Protocols
-
Azure Sentinel Integration
- Deep Threat Detection
- Analysis and Detection of Incidents
- Cloud-based SIEM
- Security Response and Orchestration
-
Detection of Incidents and Response
- Vulnerability and Vulnerability Scan
- Detection and Investigation of Danger
- Integrated SIEM-SOAR
- Risk Management and Asset Recovery
-
SOC Technologies and Instruments
- Security of Data, Applications, and Networks
- System of Security for Hosts
- Identity and Access Administration
- Next Generation Firewall
-
Zero Trust Security Measures
- Continuous Monitoring and Verification
- Danger Containment
- Automated Context Response and Collection
- Contemporary Security Frameworks
-
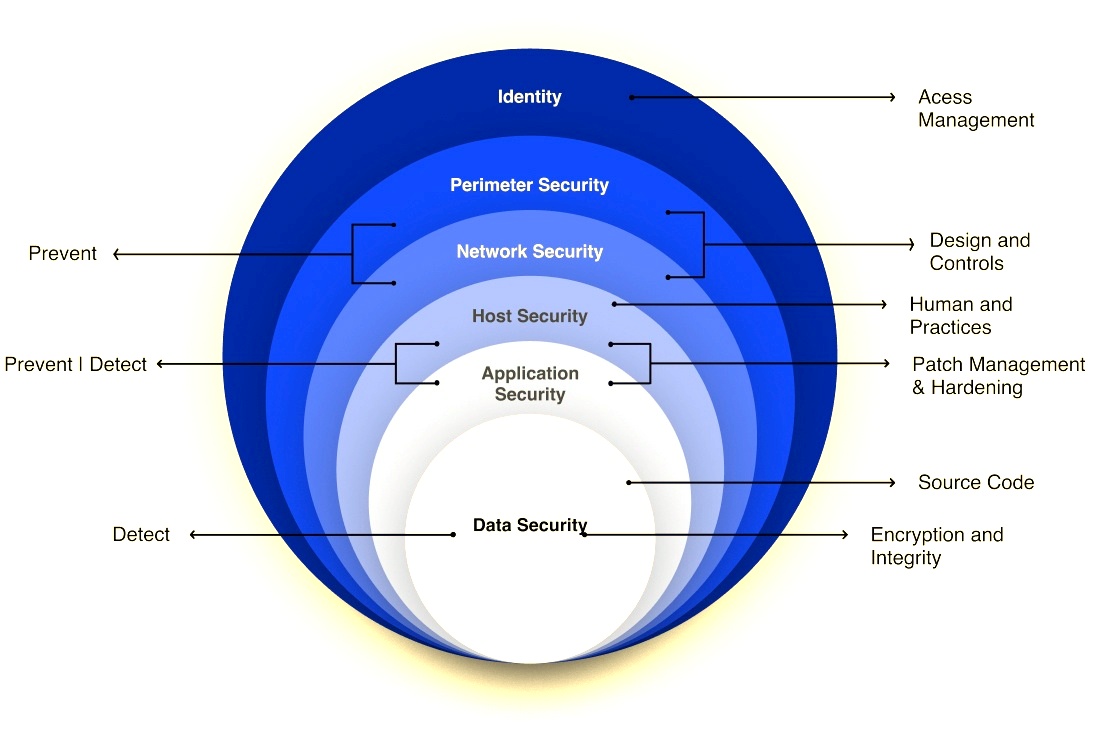
CDWT Defense-in-depth Map:
Advanced Threat Management-Powered

An Impact with Difference: Why Should Your Enterprise Partner with CDWT for Cybersecurity Transformation?
World’s largest application-focused managed service provider with dedicated Managed Security Services and advanced managed Security Operations Center Offerings
10+ years of experience, 4000+ transformation tales in 25+ countries.
800,000 EPS, 1,400 HBS, 1,200 UTMs, 7 Reg-tech Frameworks, and more than 40 Security Controls
Plus over two thousand cloud specialists and a world-class security team with industry-leading certifications: Comp TIA Security, Hyperscaler Security, Hyperscaler Platform, CISSP, OSCP, CEH, and CHFI
Intelligent automation-powered proprietary cybersecurity instruments, such as the CDWT Self Healing Operations Platform
Expertise in SOC auditing and compliance management assuring severe, flawless governance and adherence to local, national, and international legislation
Security frameworks using the MITRE ATT&CK, CIS Critical Security Controls, and others
Comprehensive 24/7 monitoring of the full IT and cloud stack for threats
Dedicated Cyber Security Incident Response Team with 24/7/365 support and problem resolution
Threat Intelligence powered by market-leading systems like Microsoft, OSINT, STIX &TAXI, MISP, etc
Expertise in establishing comprehensive SIEM-SOAR for proactive vulnerability evaluation and automated, rapid incident response
Cloud-native security with multi-cloud compatibility for the most popular cloud platforms, including AWS, Azure, GCP, Oracle, and IBM Cloud.





