Continuous Integration – Continuous Delivery (CI – CD) Security
Integrate enhanced security into the CI/CD pipelines of the enterprise. Enhance DevSecOps methods for optimum productivity and operational continuity
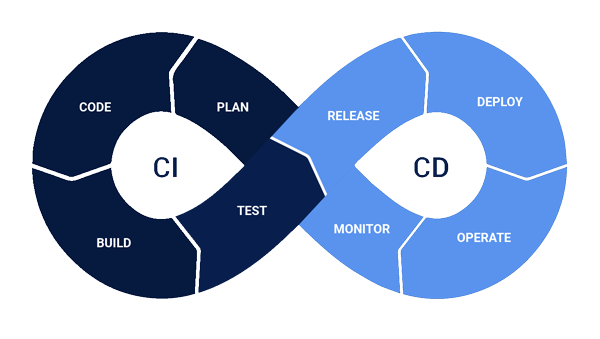
Shielding the CI/CD Pipeline Is the First Step in Establishing a Successful DevSecOps Environment.
As a discipline and culture, DevSecOps has grabbed the IT industry by storm. IT security, operational, and development teams have operated autonomously for aeons, resulting in frequent goals conflicts that have finally caused delivery schedule delays. After multiple testing and iterations, software was often released to operate important systems, only to be denied by a security filter anticipating weaknesses in the codebase.
This prompted the development of updated application, software development, testing, and deployment environments that included security checks, frameworks, and tools at each operational stage. Modernized development environments are implemented using CI/CD (Continuous Integration/Continuous Delivery) pipelines, and the DevSecOps model of a company is driven by the security integration of these pipelines.
Why Continuous Integration and Continuous Delivery (CI/CD) Security?
In order to actualize the agile corporate vision, CI/CD pipelines/solutions/platforms smoothly automate code development, testing, and deployment workflows (software development continually flows in rapid, short stages of build-test-deploy, thus the name). CI/CD tools such as Jenkins, CircleCI, TeamCity, Bamboo, GitLab, and Codeship not only help businesses modernize essential development tasks, processes, and operations, but they also store a repository of sensitive data such as platform authentications, keys, IDs and passwords, APIs, Tokens, and more. The latter information enables the CI/CD pipelines to transfer code automatically from the construction phase to the testing phase and then to the deployment phase without repetitive operator intervention.
Nevertheless, each coin has two sides. For optimum organizational security, modern security solutions and frameworks must be incorporated directly into the CI/CD pipelines in order to provide the aforementioned important benefits. With development environments and processes operating at a hyper-agile or automated rate, latent dangers may quickly crash programs, steal confidential data, and cause catastrophic losses. For enterprises to effectively deploy a DevSecOps model, CDWT, the world's biggest application-focused cloud managed services provider and a leading cybersecurity firm, puts the highest priority on CI/CD security. Integrate 24/7 threat assessment and monitoring, cutting-edge dataflow analytics, SAST-DAST procedures, source code-infrastructure-containers vulnerability scanning, automated compliance audits, and advanced threat response into development pipelines. Get 24/7/365 help from CDWT's foremost DevSecOps and CI/CD professionals.
Advantages of Implementing Specialized CI/CD Security Services and Solutions
Risk Mapping and Securing Pipelines
Integrate CI/CD pipelines and codebases, Git repositories, and secret storage centres with innovative threat monitoring and deep threat hunting, investigation, and security vulnerability assessment solutions. Detect both signature-based and unknown threats.
Streamlined Access Control and Roles
Utilize administration of access and restrictions that is uniform across development processes, infrastructure, and systems. Utilize sophisticated user analytics to identify nefarious intent. Detect irregularities by monitoring and managing user logs and using security automation and security vulnerability assessment tools.
Permissions Management
Assign positions and duties to users automatically depending on their deliverables. Easily manage permissions across numerous development environments connected with CI/CD pipelines, codebases, and code repository.
Privacy of Confidential Information
Important development environment secrets like as APIs, keys, authentication IDs, and passwords are often stored in CI/CD pipelines and solutions. Deploy security methods to safeguard such vital information on the CI/CD secrets centre or store it in separate safety vaults.
Safeguard Codebases and the Code Repository
Git repositories are excellent for storing existing code, sharing it with colleagues, analyzing and testing programs, and seeing the history of all code modifications to date. Despite the fact that these automated functions facilitate rapid code revisions, testing, and deployment, they may have vulnerabilities. According to industry best practices, protect Git repositories with extra security measures and authentication techniques.
Advanced Compliance Management for pipeline security
Conduct automated data and regulatory compliance checks across all software development environments to guarantee that all codes created, tested, and delivered through CI/CD pipelines adhere to national and international standards.
Implementation Best Practices and Immediate Strategies for CI/CD Security
Filter out, better manage, and securely store important configuration information and key secrets from CI/CD tools and solutions in vaults, even for hardcoded secrets and Infrastructure as Code data.
Implement extra security layers for essential systems and settings, such as One-Time Passwords and User Authentication methods.
Frequent deployment, distribution, and reorganisation of sensitive information and secrets across CI/CD tool files may lessen the likelihood of data loss and hacking.
Deploy sophisticated password management solutions and reset and update passwords routinely, particularly for key access systems
Clearly define, document, and administer role-based permissions and responsibilities. Access rights should be governed based on tasks and occupations.
Frequent deployment, distribution, and reorganisation of sensitive information and secrets across CI/CD tool files may lessen the likelihood of data loss and hacking.
Prevent the disclosure of secrets and the loss of sensitive data by deploying filters, firewalls, and perimeter security solutions around the CI/CD platforms.
Employ the protocols of minimal access. Sharing authentications and permissions with just users is required to limit the likelihood of secret leaks and hence undiscovered attacks.
CDWT DevSecOps and CI/CD Security End-to-End Solutions and Services
- Automated Code Analysis and Code Scanning
- Change Management
- Compliance Monitoring
- Investigating Threats
- SAST and DAST
It expedites the detection of flaws and vulnerabilities by delivering and assessing software and application code in tiny pieces or fragments on a recurring basis. Utilize specialist evaluations for penetration testing.
It allows users to contribute improvements that may increase productivity and velocity. In addition, it plays a significant role in assisting security teams in determining the effect of modifications on codes, CI/CD pipelines, implemented solutions, etc. Deploy security tools and technologies to uncover vulnerabilities and strengthen the security of the modified components.
Compliance is a crucial indicator for maintaining process security. All businesses must comply with requirements such as the General Data Protection Regulation (GDPR) and the Payment Card Industry Digital Security Standard (PCI DSS) and be ready for audits at any moment. CDWT provides comprehensive compliance audits, assessments, and framework implementations that adhere to local, national, and international laws.
Protect all secrets and sensitive data contained in CI/CD systems, including Keys, APIs, login IDs and passwords, authentication, and User access restrictions. If necessary, disperse data across numerous secure vaults and update them on a regular basis for optimum protection.
Central to a productive and efficient DevOps system are CI/CD (Continuous Integration/Continuous Delivery) pipelines. These tools and technologies automate the steps of code development, deployment, and testing. Consequently, frequent security reviews are required. SAST or Static Application Security Testing performs continuous threat monitoring and auditing on software, applications, etc. in development. DAST, or Dynamic Application Security Testing, offers improved monitoring and risk evaluations for applications and software that are actively operating or in use by various organizational divisions.
- Vulnerability Assessment (Source Code, Libraries, Infra, Containers)
- Quality Assurance
- Governance of Access and Roles
- Integrity of Data and Analytics
- Security Integration Automation
- Process Improvement
- Training
It entails a thorough evaluation and analysis of unknown threats and new vulnerabilities. To mitigate future risks and threats, analyse possible vulnerabilities across all source code, open source files, code repository, libraries, development platforms and environments, containers or VMs executing development processes, and more.
Achieve consistency and improvement with a holistic picture of security infrastructure across all codebases, storages, platforms, open source files, libraries, CI/CD pipelines, and more. Continuously monitor for detection, investigation, hunting, and analysis of threats. Ensure code and systems are risk-free and highly efficient.
Based on their duties, share roles, authentication, and platform access control with users. Easily manage identities, evaluate user behaviour, and protect systems and applications from leaks and suspicious activity.
Frequently, security tools and solutions are coupled with asset data and dataflows to provide immediate risk and vulnerability assessments. Maintain data security and integrity with ease. Compile threat monitoring and historical data from development environments and CI/CD solutions in order to acquire a thorough knowledge of the behaviour of threats, followed by the formulation of action plans.
Deploy development and operations processes using sophisticated security automation solutions and platforms such as Security Incident and Event Management (SIEM), Security Orchestration Automation and Response (SOAR), Managed Detection and Response (MDR), and others. Enhance security by design and conduct ongoing audits and analyses of latent risks and weaknesses. Automate all security management operations inside a CI/CD environment.
Collaboration across development, operations, and security workflows facilitates the optimization of duplicate procedures, dangerous gaps, and vulnerabilities. Deploy highly secure and high-performance solutions to reduce security-related losses and enhance IT return on investment over the long term.
The gap between the security team and the IT software developers must be bridged by businesses. This may be accomplished with sufficient security training and a comprehensive set of standards. With correct understanding, the management of CI/CD pipelines is simplified.
SecOps Solutions and Tools
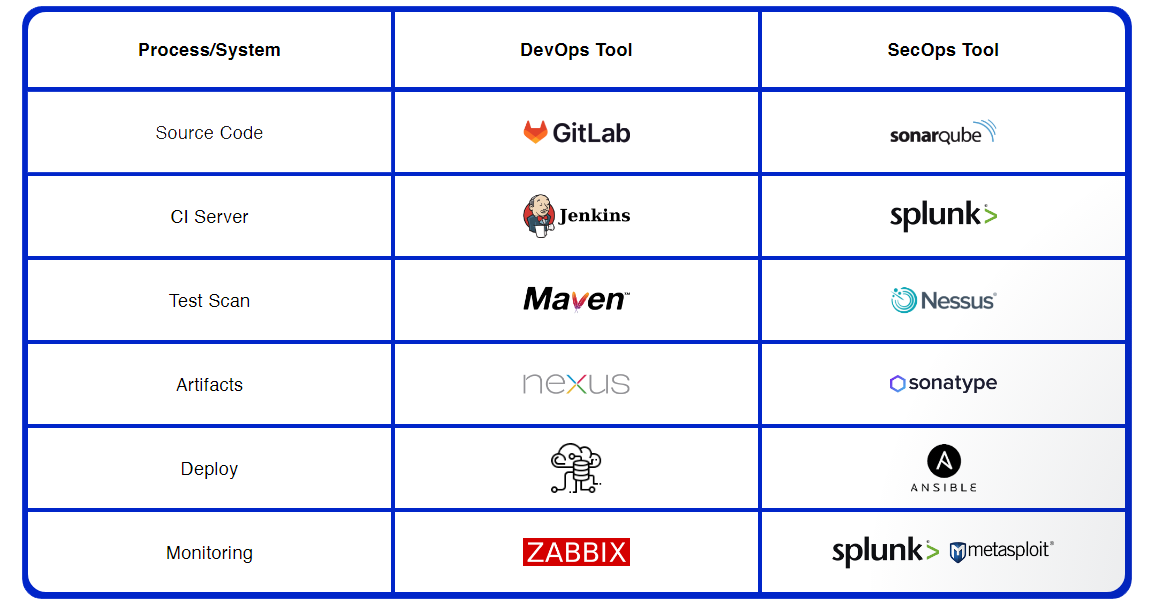
Cloud DevSecOps & CI – CD Landscape






