Application Security Testing – AST Solutions and Services
Secure Software, runtime apps, codebases, builds, CI/CD pipelines, and avoid vulnerabilities using Mobile Application Security Testing, Static Application Security Testing (SAST), and Dynamic Application Security Testing (DAST)

Automate and Report on critical vulnerabilities across Enterprise Development Landscapes
The incredible increase in the use of mobile apps, online applications, and workplace apps to modernize everyday and business ‘lifestyles’ has provided cybercriminals with an unparalleled ‘fodder-verse’ According to reports, up to fifty percent of online applications include at least one significant vulnerability. In addition, the findings indicate that it takes IT teams between six and nine months to uncover such vulnerabilities and implement the necessary corrective measures.
On the basis of the foregoing timescales, it would be erroneous to suggest that IT people are insufficiently agile. In the majority of company settings, developer and maintenance teams outweigh security engineers and experts by a significant margin. Additionally, business owners prioritize product development, delivery, and market introductions above proper testing processes. Even in the case of major enterprises with gigantic cybersecurity teams, it is difficult to manually review millions of lines of code on a frequent basis in search of a single vulnerability. Therefore, the need for extra reinforcements in modernizing cybersecurity management in the core development environments cannot be minimized.
Enhance DevOps Security Knowledge with Interactive Application Security Testing
Application Security Testing (AST) is a collection of tools, solutions, protocols, software composition analysis solutions, and procedures that automate all security administration activities pertaining to app development, testing, and deployment, including CI/CD pipelines. AST solutions often evaluate applications and their backend codebases at an astounding rate, in the millions of lines per minute. Regardless of sector or specialty, investments in Application Security Solutions and AST have multiplied over the last few years.
Solutions for Static Application Security Testing (SAST)
SAST (Static Application Security Testing) and DAST (Deep Application Security Testing) are the most typical Application Security Testing solutions (Dynamic Application Security Testing). The former, also known as White Box Testing or Inside-Out Testing, extracts programs at the source code, bytecode, or assembly code levels in order to identify/visualize and report vulnerabilities at specific lines of code.
Typically coupled with builds and internal CI/CD pipelines or software development process flows, this checks all modules, libraries, and CI/CD processes to flag security vulnerabilities in real time throughout the development phase (When an application is not running or static). The key benefit of SAST scan or SAST test, then, is that vulnerabilities may be identified at the code line level even before the code is executed, compiled, or the app development process is advanced.
Positive aspects of Static Application Security Testing (SAST Scan/Test).
Capable of analyzing and identifying mistakes throughout the earliest phases of app development. Nevertheless, may be implemented at any step of the development lifecycle.
Identifies security flaws directly at the code line levels.
Analyzes the complete app source code, codebases, CI/CD pipelines, builds, and workflows, as well as software composition analysis, to report issues throughout the development process in near real-time.
For cybersecurity teams, insightful reports with graphical representations for effective security investigation and overview of security issues
Reports vulnerabilities without compiling or executing the code.
Workflows that are highly automated for ultra-agile threat analysis
Solutions for Dynamic Application Security Testing (DAST)
DAST, or Dynamic Security Testing, employs a concept distinct from that of Blackbox Testing. In this approach, DAST tools do not have access to application source code, data flow, libraries, protocols, builds, or CI/CD pipelines. DAST solutions imitate malicious assaults or synthetic threats to attempt to break into a functioning application from the Outside-in or outside (dynamic analysis - runtime application self-protection).
For instance, DAST tools may reproduce malicious programmes and inject them into the application in order to identify injection application vulnerabilities in the operating application or platform. This enables developers and application teams to recognise unanticipated dangers and conditions that may occur owing to limits in their app security deployment tactics rather than code flaws. In addition, since the DAST Scan or DAST Test happens during application runtime, it offers a superb model for real-world settings coupled with dynamic scenarios and use-cases for simulating security concerns.
Positive aspects of Dynamic Application Security Testing (DAST Scan/Test).
Simulation of external assaults and security flaws in the existing development environment. Aids in spotting unidentified dangers
Performs automated vulnerability testing, evaluation, and analysis
Simulates dangers and examines app runtime security
Insightful reporting of the app's susceptibility to common risks, assaults, and weaknesses
Until then, app security teams will be able to identify and resolve concerns more quickly.
Assist in the development of a long-term cybersecurity plan based on realistic threat modelling.
Fully automatic resolution
A Comparison between Static Application Security Testing (SAST) & Dynamic Application Security Testing (DAST)
SAST
-
White Box Testing: SAST tools examine from the inside out all source code files, codebases, libraries, and CI/CD processes.
-
Works only while a programme is inactive; realtime software development is ineffective Lifecycle
-
Early detection of security vulnerabilities and threats in software development.
-
Because flaws are spotted in the source code at the code line level, they are less expensive to rectify.
-
Examines every programme at the source-code level.
-
In 90 days, a successful Internet-based B2B marketplace system was produced.
-
DAST
-
Black Box Testing: Deploys simulated assaults to infiltrate the application from the outside without integrating internal codebases.
-
Deployed when an application is in operation
-
Led a team of twelve resources, focusing on Siebel administration, automation of existing processes, concurrent development methods/strategies and resource management
-
Comparatively more costly since the vulnerability site must be further evaluated if problems are found.
-
Typically relevant exclusively to web applications
-
Independent of the language or fundamental platforms the application was developed on.
-
Interactive Application Security Testing Is the Foundation of a Prosperous DevSecOps Model
As a discipline and culture, DevSecOps has grabbed the IT industry by storm. IT security, operational, and development teams have operated autonomously for aeons, resulting in frequent goals conflicts that have finally caused delivery schedule delays. After multiple testing and iterations, software was often released to operate important systems, only to be denied by a security filter anticipating weaknesses in the codebase. This prompted the development of updated application, software development, testing, and deployment environments that included security checks, frameworks, and tools at each operational stage. The foundation of a company’s DevSecOps paradigm is driven by severe Application Security Testing solutions, such as SAST and DAST, applied to modernised development environments.
End-to-end CDWT DevSecOps and Application Security Testing (AST) Services and Solutions
- Automated Code Analysis and Code Scanning
- Change Management
- Compliance Monitoring
- Investigating Threats
- SAST and DAST
It expedites the detection of flaws and vulnerabilities by delivering and assessing software and application code in tiny pieces or fragments on a recurring basis. Utilize specialist evaluations for penetration testing.
It allows users to contribute improvements that may increase productivity and velocity. In addition, it plays a significant role in assisting security teams in determining the effect of modifications on codes, CI/CD pipelines, implemented solutions, etc. Deploy security tools and technologies to uncover vulnerabilities and strengthen the security of the modified components.
Compliance is a crucial indicator for maintaining process security. All businesses must comply with requirements such as the General Data Protection Regulation (GDPR) and the Payment Card Industry Digital Security Standard (PCI DSS) and be ready for audits at any moment. CDWT provides comprehensive compliance audits, assessments, and framework implementations that adhere to local, national, and international laws.
Protect all secrets and sensitive data contained in CI/CD systems, including Keys, APIs, login IDs and passwords, authentication, and User access restrictions. If necessary, disperse data across numerous secure vaults and update them on a regular basis for optimum protection.
Central to a productive and efficient DevOps system are CI/CD (Continuous Integration/Continuous Delivery) pipelines. These tools and technologies automate the steps of code development, deployment, and testing. Consequently, frequent security reviews are required. SAST or Static Application Security Testing performs continuous threat monitoring and auditing on software, applications, etc. in development. DAST, or Dynamic Application Security Testing, offers improved monitoring and risk evaluations for applications and software that are actively operating or in use by various organizational divisions.
- Vulnerability Assessment (Source Code, Libraries, Infra, Containers)
- Quality Assurance
- Governance of Access and Roles
- Integrity of Data and Analytics
- Security Integration Automation
- Process Improvement
- Training
It entails a thorough evaluation and analysis of unknown threats and new vulnerabilities. To mitigate future risks and threats, analyse possible vulnerabilities across all source code, open source files, code repository, libraries, development platforms and environments, containers or VMs executing development processes, and more.
Achieve consistency and improvement with a holistic picture of security infrastructure across all codebases, storages, platforms, open source files, libraries, CI/CD pipelines, and more. Continuously monitor for detection, investigation, hunting, and analysis of threats. Ensure code and systems are risk-free and highly efficient.
Based on their duties, share roles, authentication, and platform access control with users. Easily manage identities, evaluate user behaviour, and protect systems and applications from leaks and suspicious activity.
Frequently, security tools and solutions are coupled with asset data and dataflows to provide immediate risk and vulnerability assessments. Maintain data security and integrity with ease. Compile threat monitoring and historical data from development environments and CI/CD solutions in order to acquire a thorough knowledge of the behaviour of threats, followed by the formulation of action plans.
Deploy development and operations processes using sophisticated security automation solutions and platforms such as Security Incident and Event Management (SIEM), Security Orchestration Automation and Response (SOAR), Managed Detection and Response (MDR), and others. Enhance security by design and conduct ongoing audits and analyses of latent risks and weaknesses. Automate all security management operations inside a CI/CD environment.
Collaboration across development, operations, and security workflows facilitates the optimization of duplicate procedures, dangerous gaps, and vulnerabilities. Deploy highly secure and high-performance solutions to reduce security-related losses and enhance IT return on investment over the long term.
The gap between the security team and the IT software developers must be bridged by businesses. This may be accomplished with sufficient security training and a comprehensive set of standards. With correct understanding, the management of CI/CD pipelines is simplified.
DevSecOps Solutions and Tools
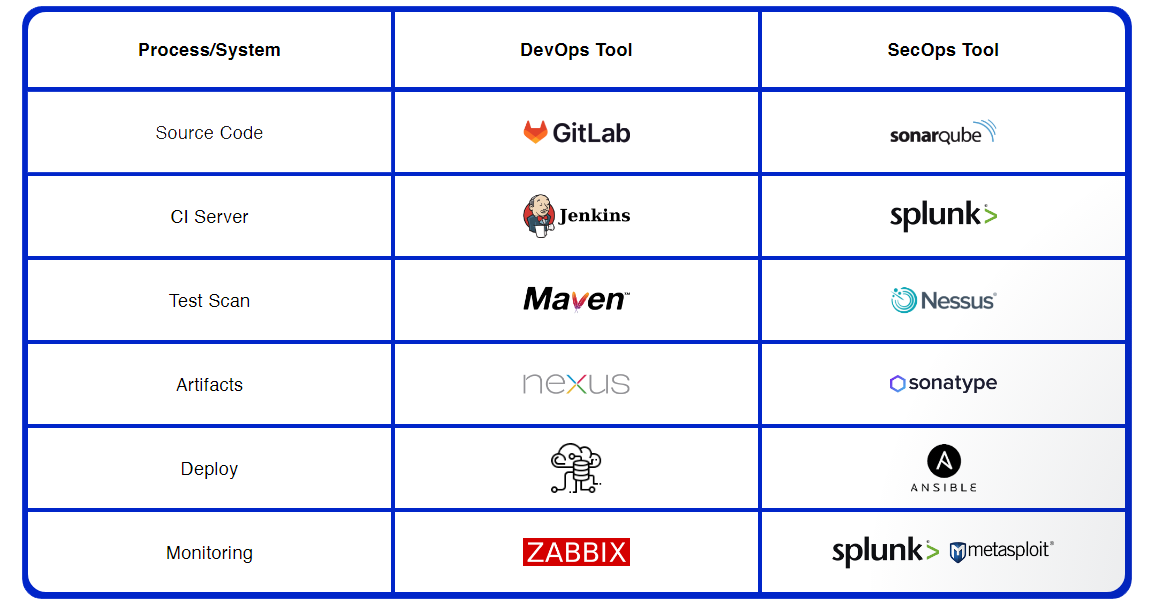
Cloud DevSecOps Landscape

What Makes CDWT’s DevSecOps Security Solutions and Services Unique?
The world's biggest Application-focused Managed Cloud Services Provider and a leader in managed cybersecurity. Dedicated security evaluation services.
12+ years of service to 4000+ corporations, including 60+ Fortune 500 companies, in 25+ countries spanning the Americas, Europe, Middle East, and APAC.
More than 40 Security Controls, twenty Centres of Excellence, and two thousand worldwide cloud specialists
Pre-met compliance demands for local, national, and international compliance regulations, such as IRAP, GDPR, HIPAA, SAMA, CSA, GXP, and ISO Certifications.
3200 UTMs, 13000 HBSS, 800000 EPS
Seven Security frameworks using the MITRE ATT&CK, CIS Critical Security Controls, and more
Comprehensive 24x7 monitoring of cyber security
Advanced Managed Detection and Response Solutions Automated Security Solutions for threat prediction, detection, and response (MDR)
Expertise in managed SOC (Security Operations Center) services and solutions on a global scale.
DevSecOps-specific portfolio
Cybersecurity Consulting, Cybersecurity Assessment, and Audit Reporting Services for the Entire IT Stack and Cloud Infrastructure.
Advanced Cybersecurity Incident and Response Team (CSIRT) for CDWT
Threat Intelligence powered by Industry-leading platforms such as Microsoft, OSINT, STIX&TAXI, MISP, etc. and CDWT Threat experts
Considerable threat management knowledge in protecting big and complex settings and using the sophisticated features of industry-leading technologies and Cloud-Native Security products.
Expertise in building and administering comprehensive SIEM - assisting organisations in proactively assessing vulnerabilities and automating and accelerating incident response.
Application Security Testing – AST – FAQ’s
That is, malicious assaults that may occur owing to code-based deficiencies. The benefit of SAST is that monitoring and audits are performed automatically throughout the development process, warning developers of any code-based restrictions that might compromise security. The thorough SAST reports include charts, graphs, and insights that highlight issues at the code level.